Static vs Dynamic Security Testing: Key Differences and Use Cases
In today's hyper-connected digital world, application security is more critical than ever. With the increasing number of cyber threats targeting software vulnerabilities, security testing has become a non-negotiable aspect of the software development life cycle (SDLC). Two of the most common and essential types of security testing are Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST). Each has its strengths, limitations, and ideal use cases. Understanding the differences between these two testing methodologies is essential for organizations looking to enhance their security posture and for security testing companies striving to deliver the best solutions to their clients.
What is Static Application Security Testing (SAST)?
SAST, or Static Application Security Testing, is a white-box testing method that analyzes source code, bytecode, or binary code for vulnerabilities without executing the program. It is typically performed early in the development process, often during the coding or build phase.
SAST tools scan the codebase to identify security weaknesses such as SQL injection, cross-site scripting (XSS), buffer overflows, and insecure APIs. Since it operates at the code level, SAST provides developers with detailed insights into the exact location of vulnerabilities, enabling faster remediation.
Key Features of SAST:
- Early detection: SAST can be integrated into the development environment to catch vulnerabilities before the application is compiled or deployed.
- Access to source code: It requires access to the application's source or compiled code.
- Speed: Can be run quickly, especially when only parts of the codebase change.
- Compliance: Helps in meeting security compliance requirements by providing reports and audit trails.
What is Dynamic Application Security Testing (DAST)?
DAST, or Dynamic Application Security Testing, is a black-box testing method that analyzes a running application to identify security vulnerabilities. It is typically performed later in the SDLC, such as during the testing or staging phase.
DAST tools simulate external attacks on a web application to uncover issues like authentication problems, server configuration errors, data leakage, and input/output validation errors. Unlike SAST, DAST does not require access to the source code, making it suitable for third-party applications or legacy systems.
Key Features of DAST:
- Real-time testing: DAST evaluates the application in its running state, providing insight into how it behaves under real-world attack scenarios.
- No source code needed: Ideal for organizations testing third-party applications or when source code is unavailable.
- Comprehensive testing: Effective at identifying runtime and environment-related vulnerabilities.
- Language agnostic: Can test applications regardless of the programming language used.
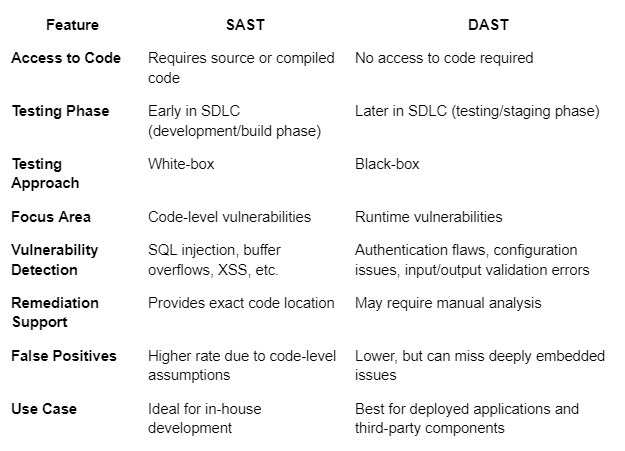
Key Differences Between SAST and DAST
Use Cases of SAST
- During Development: SAST is best used during the development phase to catch vulnerabilities before they become ingrained in the codebase. Developers can integrate SAST tools with their IDEs or CI/CD pipelines for continuous scanning.
- Code Reviews: Security testing companies often employ SAST during manual or automated code reviews as part of secure code auditing.
- Regulatory Compliance: SAST helps meet requirements for standards like OWASP Top 10, ISO 27001, and PCI DSS, which often demand thorough code-level analysis.
- Early Bug Detection: Identifying bugs early in the SDLC reduces the cost of remediation and improves code quality.
Use Cases of DAST
- Pre-Deployment Testing: DAST is most effective when used before software goes into production. It simulates how attackers might exploit an application in its deployed state.
- Security Regression Testing: DAST helps ensure that previously fixed vulnerabilities have not re-emerged due to new code changes.
- Penetration Testing Support: Security testing companies often use DAST tools to complement manual penetration tests, providing automated scanning to uncover common vulnerabilities.
- Third-Party Application Security: When testing applications developed by external vendors or where source code access is restricted, DAST provides a practical solution.
Combining SAST and DAST for Maximum Security
While SAST and DAST serve different purposes, they are most powerful when used together in a comprehensive security testing strategy. By integrating both methods into the SDLC, organizations can:
- Detect a broader range of vulnerabilities
- Cover both code-level and runtime security issues
- Ensure continuous feedback and remediation throughout development
- Strengthen compliance posture
Many leading security testing companies recommend combining these tools as part of a DevSecOps approach, integrating security seamlessly into the CI/CD pipeline.
Challenges and Considerations
- False Positives/Negatives: Both SAST and DAST can produce false positives or negatives. It's important to validate findings manually or use advanced tools with better accuracy.
- Tool Complexity: Selecting and configuring the right tools requires expertise. Security testing companies can help with implementation and tuning.
- Performance Overhead: Running security tests, especially DAST, may affect application performance temporarily.
- Skill Gaps: Developers and testers may need training to interpret results effectively and fix issues.
Choosing the Right Approach
When deciding between SAST and DAST, consider the following:
- Development Stage: Use SAST early, DAST later.
- Access to Code: If code is available, use SAST. If not, DAST is your best bet.
- Regulatory Needs: Use SAST to meet code-level compliance requirements.
- Risk Profile: Combine both methods for a high-assurance security posture.
Security testing companies often conduct risk assessments to recommend the right mix of SAST and DAST based on organizational needs, development practices, and threat landscape.
Conclusion
SAST and DAST are not competing technologies but complementary tools in the security tester's arsenal. Understanding their differences, strengths, and ideal use cases enables organizations to make informed decisions about securing their applications. By leveraging both static and dynamic testing, businesses can build more secure software, reduce vulnerabilities, and protect customer data more effectively.
Partnering with experienced security testing companies can make this process more streamlined and effective, ensuring tools are correctly implemented, findings are accurately interpreted, and vulnerabilities are swiftly addressed.
FAQs
Q1. What is the main difference between SAST and DAST?
SAST analyzes the application's source code for vulnerabilities before it's run, while DAST tests the application during runtime to find exploitable issues without needing access to the source code.
Q2. Can I use both SAST and DAST in one project?
Yes, using both provides broader coverage and is a recommended best practice in modern DevSecOps pipelines.
Q3. Are there tools that support both SAST and DAST?
Some integrated platforms offer both functionalities, but most organizations use specialized tools for each. Security testing companies often help integrate these into a cohesive workflow.
Q4. Which testing method is better for compliance?
SAST is often more suitable for meeting detailed compliance requirements as it provides in-depth code-level analysis and reporting.
Q5. Do I need coding knowledge to run SAST or DAST?
Running SAST usually requires some coding knowledge, especially to fix issues. DAST can be used with less coding expertise, as it focuses on application behavior.
